Kill the Lights: Taking Control of Digital Privacy
A few months ago I installed the latest Android beta, excited by its new design language. Three days later I had to uninstall it when I got stranded at the grocery store thanks to the Uber app crashing. However, in that short time I benefitted from another new feature (that iPhone users already enjoy) wherein the OS would notify me when an app used the clipboard. Excited by this, I took the same ideas and ported them to Chrome via an open source extension called Kill Switch.
Browsers are easily one of the most impressive pieces of consumer technology in general use today. Not only do they offer developers a myriad of tools to create powerful applications with ease, they do so with a focus on security that is unparalleled in modern software development. With protections at every level of abstraction and a speedy update cycle, most users are at little risk of having their data compromised by bad actors.
At the same time, the sheer quantity of APIs exposed means that the potential attack surface is huge. Even then, just because something is not a security risk, doesn’t mean it isn’t a privacy risk. A great example of this is WebGL, which has been used historically as a means of fingerprinting devices due to the eccentricities of different hardware. Obviously, this cannot be used to actually leak data directly, but it can be used to coarsely track people, thus violating user’s privacy.
Just as with security, browsers are continuously adding mitigations to prevent these types of abuses. However, they do so opaquely and offer little insight to end users about what risks they are being exposed to. Since privacy is inherently personal, and every individual has different thresholds of acceptability, I believe that users should have the tools and opportunity to easily control their exposure.
Kill Switch
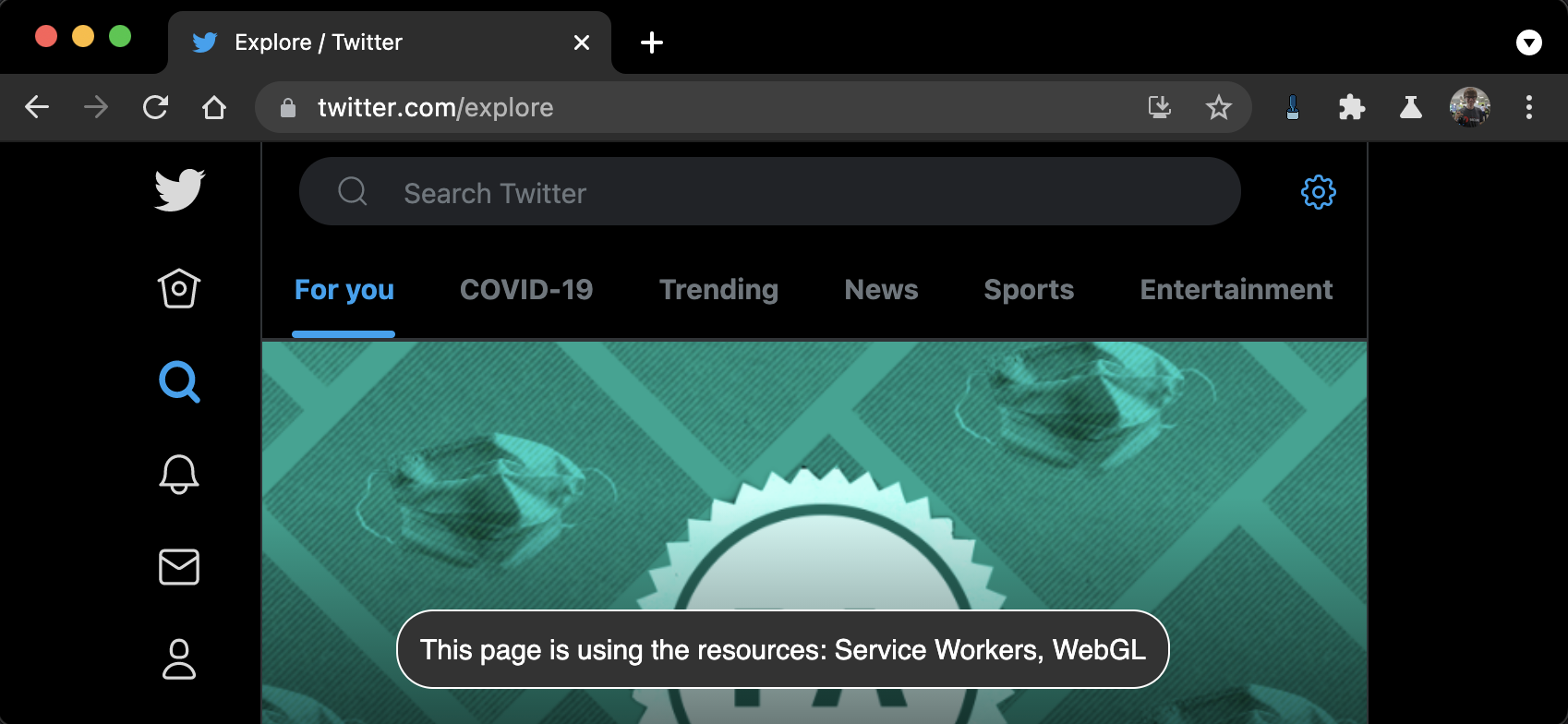
For my own use, and for those with similar proclivities, I took several of these abusable APIs and wrote a Chrome Extension to monitor them. Per-site, it provides users with several configurations options for each of these APIs. Namely, it can unconditionally enable or disable them, notify the user when they’re being invoked, or prompt the user for permission on first access.
This is the part, unfortunately, where I need to reiterate that this is intended to be a privacy tool, not a security one. Although I take steps to run Kill Switch before any of the other scripts on the page, a dedicated developer could certainly find ways to bypass it. As a consequence of these adversarial cases, if you are worried about any particularly sensitive APIs, please disable them at the Browser, OS, or even hardware levels. Any of those will provide you with far better guarantees.
With that said, however, for casual web browsing, Kill Switch is an unobtrusive way to get unique insight into what websites are collecting on you, and in many cases will give you the power to put a stop to it. Plus, it’s fully open source and open to contributions!
The Bigger Picture
At the end of the day, Kill Switch is neither novel, nor technically impressive. Yet, I think it’s a useful piece in the ongoing dialogue of digital privacy in an increasingly technocratic internet. Over the next few years this conversation is only going to become more difficult and more important.
If this is something that interests you, I would encourage you to think about what digital privacy looks like, and how we can start to move in the right direction. Projects like these are a good way to prototype ideas and experiences, but even just organizing your thoughts into a blog post or article can be a great way to spur discussion. If you do, please share it with me on twitter or by email! I’m excited to see where the next few years take us.